You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
QANTAS Cyber Incident
- Thread starter Princess Fiona
- Start date
- Featured
- Joined
- Jul 8, 2007
- Posts
- 3,012
- Qantas
- Platinum 1
- Virgin
- Red
- Oneworld
- Emerald
Easier to name the companies that haven't suffered a breachDid you forget Medibank, Latitude, MediSecure (lol), ClubsNSW, Service NSW, Telstra, etc?
OATEK
Senior Member
- Joined
- Apr 12, 2013
- Posts
- 5,785
Oh, I think that is harsh! I am sure they monitor the storage requirements for the collected data! How much gets read, yes that is the question. Assume a growing involvement of AI in SIEM review, but where QF are up to is anybody's guess."Strengthen system monitoring and detection" is most likely sends the system feed to another instance of SIEM somewhere else ...... But then no one actually monitors the SIEM anyway.
Daver6
Enthusiast
- Joined
- Dec 31, 2011
- Posts
- 12,298
- Qantas
- Platinum
- Virgin
- Silver
It's often the internal systems that are the least protected, as application teams heavily rely on network-level security and ignore application-level security.
Thankfully that's the legacy way of thinking about it and more and more companies are trying to move towards ZTA. Problem is, most don't understand it or think ZTA is a single product.
Post automatically merged:
Easier to name the companies that haven't suffered a breach
Let me compile that list quickly. Oh wait...it's more like an empty set.
Probably put companies into two lists. Those that are aware they've been breached and those that have been breached but they just don't know it.
Above comment is a tongue in cheek, but probably a little closer to the truth than we'd like.
- Joined
- Jan 26, 2011
- Posts
- 30,301
- Qantas
- Platinum
- Virgin
- Red
I forgot my password earlier this year and tried to change it do year (not month) and it wouldn't allow it.They certainly have in the past, last year I found out my elderly dad had his pin as DDMM of his birthday and forced him to change it to something not obvious.
Read our AFF credit card guides and start earning more points now.
AFF Supporters can remove this and all advertisements
Is that less or more likely than what someone else above hoped for that execs would be held responsible and their bonuses confiscated?Someone over on OzBargain wanted them to gift 50k points "as an apology". Good luck getting that!
I mean at least that alone seems to have been enough to (maybe) prevent a bunch of account fraud ala what happened to Virgin Velocity awhile back before they bothered adding it.Yes.. 2FA...
oz_mark
Enthusiast
- Joined
- Jun 30, 2002
- Posts
- 22,151
Easier to name the companies that haven't suffered a breach
There's two types of companies
1) Those that have had a data breach
2) Those that don't know they've had a data breach
- Joined
- Jan 26, 2011
- Posts
- 30,301
- Qantas
- Platinum
- Virgin
- Red
Well, I hold an account for son who has never used it. Zero status. Zero points. He got this email. We, on the other hand, both active and WP have received - nothing.Received the first email about the problem:
Now wait and see for a second
kangarooflyer88
Established Member
- Joined
- May 29, 2021
- Posts
- 4,651
- Qantas
- Gold
- Virgin
- Silver
- Oneworld
- Sapphire
- Star Alliance
- Gold
Will be interesting to see how the EU responds to this alleged breach and whether a fine will be levied.
Aeryn
Active Member
- Joined
- Feb 26, 2025
- Posts
- 787
- Qantas
- Platinum
- Virgin
- Red
- Oneworld
- Emerald
Well, I hold an account for son who has never used it. Zero status. Zero points. He got this email. We, on the other hand, both active and WP have received - nothing.
I got the generic email which just says same thing as the website, what I want to know is specifically if my own details were in the 6M records breached or not.
Last edited:
oz_mark
Enthusiast
- Joined
- Jun 30, 2002
- Posts
- 22,151
That would be 6 million records, not 6k.I got the generic email which just says same thing as the website, what I want to know is specifically if my own details were in the 6k records breached or not.
- Joined
- Jul 8, 2007
- Posts
- 3,012
- Qantas
- Platinum 1
- Virgin
- Red
- Oneworld
- Emerald
Give it time. For such a massive email send, it's pretty normal that it will be split into smaller batches that are sent over an extended period of time.We, on the other hand, both active and WP have received - nothing.
Last edited:
Flyerwin
Active Member
- Joined
- Jul 23, 2022
- Posts
- 569
- Qantas
- Platinum
- Virgin
- Platinum
- Oneworld
- Emerald
Experian via Commonwealth Bank.Equifax ?
MELso
Established Member
- Joined
- Nov 12, 2011
- Posts
- 1,458
- Qantas
- Gold
- Virgin
- Red
- Oneworld
- Sapphire
Indeed - given that they don't actually use the DOBs anymore, I don't know why (other than sheer inertia/laziness) they've been retained.leaking birth dates is a huge security violation, I'm surprised how their email attempts to downplay the severity
I wish more people were aware of how sensitive & important it is to guard your birth date
(I was recently reminded that my DOB was incorrect because it was pre-populated on a Qantas Health Insurance quote, but can't remember the last time they had any other use).
- Joined
- Jun 1, 2014
- Posts
- 5,509
Mine went to spam because it came from an email address I’ve not seen Qantas use before.Well, I hold an account for son who has never used it. Zero status. Zero points. He got this email. We, on the other hand, both active and WP have received - nothing.
Way to give customers peace of mind.
gtrod
Junior Member
- Joined
- Sep 3, 2019
- Posts
- 47
- Qantas
- Platinum
- Virgin
- Silver
- Oneworld
- Emerald
- Star Alliance
- Gold
You don't need to worry about brute forcing individual accounts when you have so many pairs of FF# and surname.Brute forcing 4 digit pins is not an option as accounts quickly get locked out but having FF# and Surname significantly lowers the bar.
You get 3 chances to guess the right number. That means for each account they try to access they have a 1 in 3,333 chance of guessing correctly.
They have 6,000,000 accounts.
So just guessing 3 numbers for each of the 6mil accounts will be successful 1,800 times.
MELso
Established Member
- Joined
- Nov 12, 2011
- Posts
- 1,458
- Qantas
- Gold
- Virgin
- Red
- Oneworld
- Sapphire
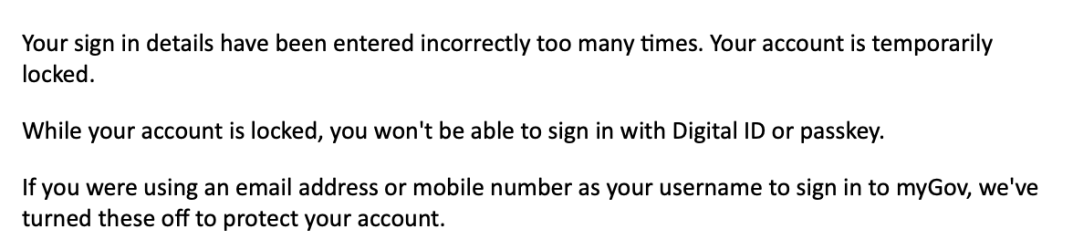
They try and brute force MyGov all the time. The pro tip is to switch off your email address as a username (which they seem to have done), set up a passkey and turn off passwords.I just got locked out of my MyGov account - I wonder if it's related to the hack. Hackers already trying to brute force accounts?
View attachment 454780
Aeryn
Active Member
- Joined
- Feb 26, 2025
- Posts
- 787
- Qantas
- Platinum
- Virgin
- Red
- Oneworld
- Emerald
Mine went to spam because it came from an email address I’ve not seen Qantas use before.
Way to give customers peace of mind.
Weird mine came from the usual Qantas Frequent Flyer address
Become an AFF member!
Join Australian Frequent Flyer (AFF) for free and unlock insider tips, exclusive deals, and global meetups with 65,000+ frequent flyers.AFF members can also access our Frequent Flyer Training courses, and upgrade to Fast-track your way to expert traveller status and unlock even more exclusive discounts!

AFF forum abbreviations
Wondering about Y, J or any of the other abbreviations used on our forum?Check out our guide to common AFF acronyms & abbreviations.
Currently Active Users
- hydrabyss
- Ansett Nostalgic
- Happy Dude
- Arkana
- aussieboozer
- SYD
- Beer_budget
- Foz
- Harrison_133
- *A Flyer
- exceladdict
- jboy90
- Triben
- GrahamBRI
- Grrr
- jabba
- Pete98765432
- HealthyPotato
- mrsterryn
- agrias
- DejaBrew
- randompunter
- FlyingFiona
- Vekor
- alviau
- madrooster
- hutch
- RadioBusinessTraveller
- downgraded
- pmdg7444
- pauly7
- Tindersinder
- Ubern
- LionKing
- ghinx
- Forg
- CMA222
- TheRealTMA
- RSD
- markis10
- IainF
- logos 01
- DaveLoftus
- Rich
- sihyonkim
- daft009
- vm3365
- Nic
- Austman
- Doug_Westcott
Total: 2,272 (members: 76, guests: 2,196)