- Joined
- Sep 20, 2018
- Posts
- 4,658
- Qantas
- Platinum
It's basically a case of one group of FF members arguing "...I'm more heavily impacted so you should have communicated to me earlier instead of pushing a "nothing to see here" agenda with those who had nothing overly meaningful leaked" vs another group of FF members who would be arguing "...why did you keep me waiting and worrying for so long before telling me I was on the lower end of the impact scale?"
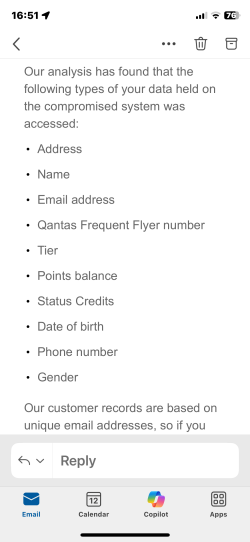
So I got email #3 at 2230 last night. Scored a healthy 10/11. I’ve never had a meal preference. Mr Seat 0A got 9/11 - gender and meals missing. Felt angry.Here’s another twist in the tail…
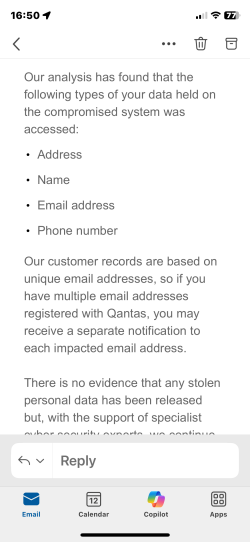
Mrs Jimmy got the 3rd email on Wednesday saying Name & Email data leaked.
Now today, Friday at about 5pm (trash time), she gets another one (4th), saying ooops, we leaked your Phone Number too…
Edit: And now I have a 4th email to also include Phone Number.
Then 30 mins later emailed #4. With only 4 items. Felt confused.
I bet QF did not select angry and confused as words they wanted their brand to evoke with customers the last time they did a brand workshop.
Come on QF not good enough.
Edited to resize the photos
Last edited: